How to Avoid Smartphone Phishing Attacks in 2025: Advanced Strategies for Real Protection
Smartphone phishing attacks have evolved significantly in 2025, becoming more sophisticated and harder to detect. You’ve probably heard basic advice like avoiding suspicious links and enabling multi-factor authentication, but these measures are no longer enough. If you truly want to protect your smartphone from phishing attacks, you need to adopt advanced, proactive strategies that address the latest threats. In this article, I’ll guide you through these advanced tactics, using real-world examples and actionable advice to enhance your smartphone security.
Table of Contents
Understanding the Problem
Phishing attacks are deceptive attempts by cybercriminals to obtain sensitive information by impersonating trustworthy entities. In 2025, these attacks have evolved significantly, using more advanced techniques, such as AI-generated emails, deepfake technology, and malicious QR codes. According to the Anti-Phishing Working Group’s report, over 1 million phishing attacks occurred in the first quarter of 2025, with a significant rise in attacks targeting online payment and financial sectors. These statistics paint a clear picture: phishing is becoming a more targeted and dangerous threat.
Phishing attacks often exploit human psychology, creating a sense of urgency or fear. For example, fake messages that look like they’re from your bank or delivery service may trick you into providing personal information or clicking on harmful links. Given how these attacks are becoming more sophisticated, it’s crucial to reassess your approach to smartphone security and go beyond basic measures.
The Growing Threat of Phishing Attacks
There are more than just hypothetical issues with phishing attacks. In Mexico alone, almost 13 million people fell victim to cybercrime, particularly phishing, in the past seven years. Financial data, personal information, and even unauthorized access to bank accounts have been lost as a result of these attacks. Anyone who would think they are immune should be warned by the shocking numbers.
Phishing attacks on smartphones are particularly dangerous because of how common and convenient they are in daily life. These gadgets store so many emails, banking apps, texts, and other private information that losing access to them or having your data compromised can have catastrophic consequences. The sophistication of phishing attempts makes them difficult to detect, and traditional security measures might no longer be adequate.
Therefore, if you believe that you can stay safe from phishing attacks by simply avoiding suspicious URLs, you are mistaken. It’s insufficient now. The attackers are more skilled, and the stakes are higher. A multi-layered security strategy that actively combats these changing threats is required.
Advanced Strategies to Protect Your Smartphone
In 2025, you should consider implementing these innovative strategies to defend your smartphone against phishing attacks. These solutions go beyond the basics and place an emphasis on proactive protection.
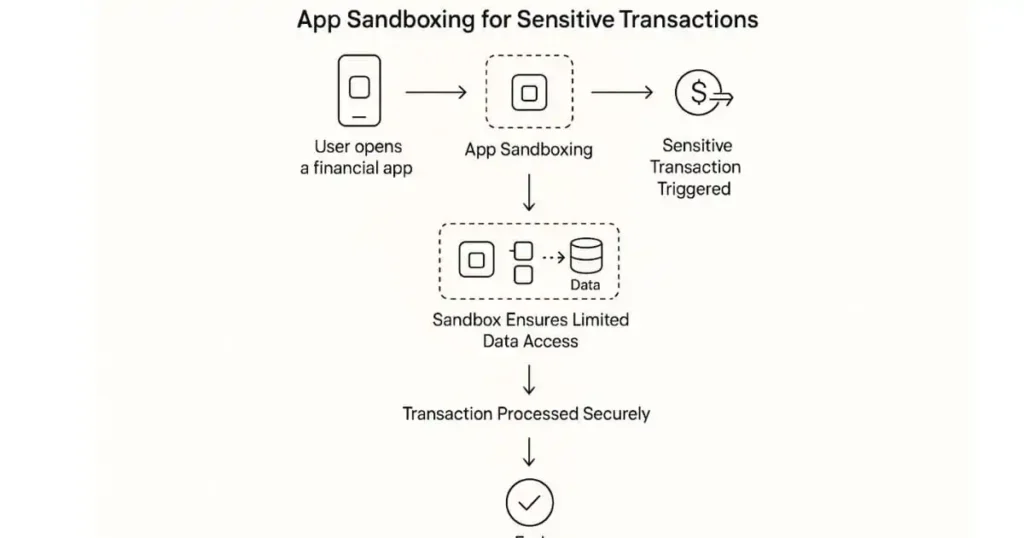
1. App Sandboxing for Sensitive Transactions
App sandboxing isolates applications from each other, preventing them from accessing sensitive data or interacting with other apps without permission. This is particularly important for financial transactions, where security is paramount.
Implementation Tips:
iOS: Thanks to Apple’s App Sandbox feature that prevents apps from accessing data outside of the designated container. To keep your financial apps safe, turn on this feature and update them often.
Android: Android conducts app sandboxing by default at the operating system level; developers do not “implement” it in the same way that they could add a library. Instead, Android’s security mechanism isolates all applications automatically, or you can utilize apps that support security features like Scoped Storage. By limiting the data that the software may access, this adds another layer of protection.
Since it lessens the chance that malware will obtain personal data from other programs, app sandboxing is an effective defense against phishing.
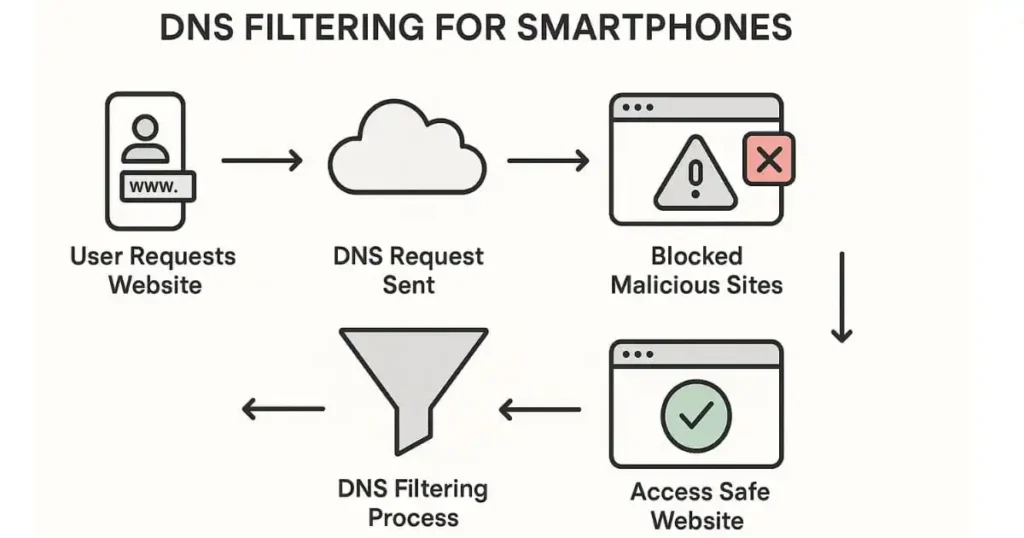
2. DNS Filtering for Smartphones
DNS filtering stops access to malicious websites by intercepting DNS requests and preventing connections to known risky domains. Even if you accidentally click on a malicious link, you can ensure that your smartphone won’t connect to harmful websites by using DNS filtering services.
Implementation Tips:
iOS devices:
For iOS 14 and Above:
- Open the Settings app.
- Tap on Wi-Fi and then the ‘i’ icon next to your connected network.
- Scroll down and tap Configure DNS.
- Select Manual.
- Tap Add Server and enter
1.1.1.3for Cloudflare’s DNS. - Tap Save.
Note: If you’re using iOS 17, Safari’s Private Browsing mode can override your DNS settings, perhaps bypassing your configured DNS filtering. To avoid this, try disabling Advanced Tracking and Fingerprinting Protection in Safari’s settings.
Android Devices:
For Android 9 (Pie) and Above:
- Open the Settings app.
- Navigate to Network & Internet > Advanced > Private DNS.
- Select the Private DNS provider hostname option.
- Enter
1dot1dot1dot1.cloudflare-dns.comfor Cloudflare’s DNS-over-TLS. - Tap Save.
This configuration ensures that your DNS queries are encrypted, providing an additional layer of security against phishing attacks.
- For Older Android Versions (Before Pie):
- Open the Settings app.
- Go to Wi-Fi and long-press your connected network.
- Tap Modify Network > Advanced Options.
- Change IP settings to Static.
- Under DNS 1, enter
1.1.1.3(Cloudflare for Families – blocks malware and adult content). - Under DNS 2, enter
1.0.0.3. - Tap Save.
The above setup improves the security of your device by preventing access to malicious and explicit domains.
Test Your DNS Settings
Once DNS filtering has been set up, you can test it by visiting a website designed to check for malware blocking, such as https://malware.testcategory.com This helps ensure that harmful websites are blacklisted and that your DNS filter is activated.
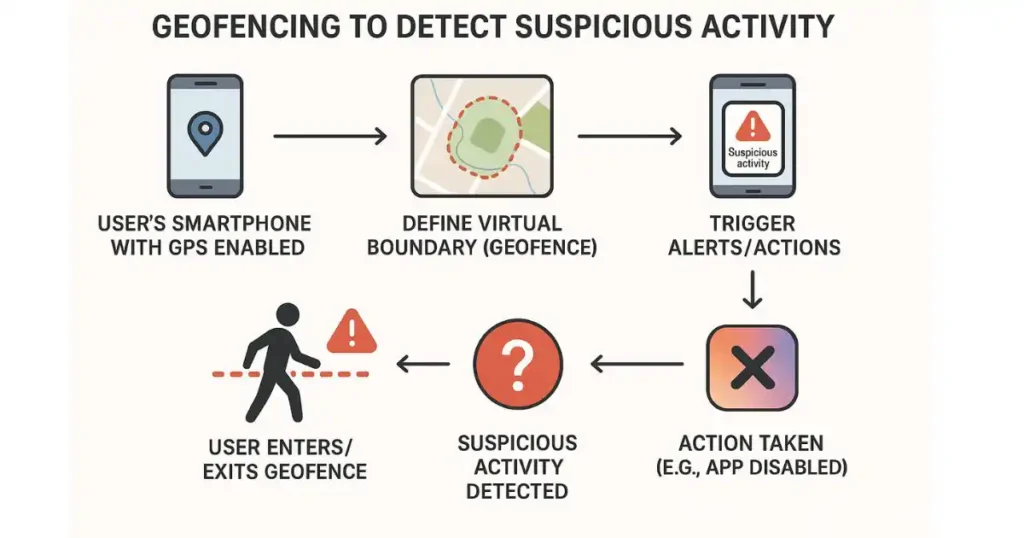
3. Leverage Geofencing to Detect Phishing Attacks
Geofencing creates virtual limits by using the GPS on your smartphone. When you enter or leave certain borders, specific actions are initiated, such as disabling specific programs or warning you of questionable activities. This can help detect phishing attacks by ensuring that your smartphone only functions normally in trusted sites.
Implementation Tips:
- Make use of apps that offer geofencing, such as Life360 or IFTTT.
- Set alerts to sound when your device enters or leaves particular areas, such as your house or place of employment.
- To develop a complete security system, combine geofencing with other security measures.
- By making sure that suspicious activity, like a sudden shift in location, sets off alarms or security measures, geofencing provides an additional degree of protection.
4. VPN Setup for Enhanced Privacy and Security
A virtual private network (VPN) conceals your IP address and shields your data from shady eyes by encrypting your internet connection. Using a VPN is essential, especially when using public Wi-Fi or accessing sensitive material
Implementation Tips:
- Always choose a reliable VPN provider with strong encryption and a strict no-logs policy.
- Be sure your VPN is always connected when using public Wi-Fi networks or accessing sensitive data.
- Keep the VPN application running in the background for ongoing security.
- A virtual private network, or VPN, reduces the likelihood of attacks on your personal information by making sure that your smartphone data is protected.
5. Behavioral Biometrics for Continuous Authentication
Behavioral biometrics analyzes patterns in your activity, such as how you type, swipe, and utilize apps, to continuously verify your identity. In addition to employing passwords, this method ensures that only you can access your device, even if a hacker manages to get onto it.
Implementation Tips:
- Activate behavioral biometrics in programs that enable it, such as BehavioSec or Zebra Medical.
- Update your apps often to ensure they are utilizing the most recent security features.
- Avoid apps that collect sensitive behavioral data (how you type, swipe, and utilize apps); before using any app, make sure to read its privacy policies.
- By regularly confirming your identity, behavioral biometrics provide an extra layer of security that is not possible with standard passwords.
6. Advanced Phishing Detection with AI
Artificial intelligence (AI) can analyze patterns in emails, messages, and websites to spot phishing attacks. AI-powered solutions enable real-time phishing attack identification, lowering the chance of falling victim compared to usual.
Implementation Tips:
- Use security programs like Lookout or Malwarebytes that detect phishing attacks using artificial intelligence.
- Turn on real-time scanning features to spot phishing attacks as they happen.
- Update your apps and operating system to benefit from the latest advancements in artificial intelligence.
AI-based phishing detection is a proactive security that constantly monitors your smartphone to identify threats as they appear.

7. Educate Yourself and Stay Informed
Last but not least, staying updated on the latest phishing attacks and developing the ability to recognize them is essential to reducing your risk. The best defense is knowledge because attackers continually modify their strategies.
Implementation Tips:
- Follow reputable cybersecurity blogs and news sources to stay up-to-date on the latest phishing attacks.
- Participate in cybersecurity awareness training programs to enhance your ability to recognize phishing attempts.
- Regularly check the security settings on your device and adjust as needed based on fresh information.
- If you stay informed, you can better spot phishing attacks and protect your smartphone from evolving threats.
Conclusion
The complexity of phishing attacks will be higher than ever in 2025, but so will defenses and strategies. You may greatly lower your risk of being a victim of these phishing attacks by putting advanced security measures in place including app sandboxing, DNS filtering, geofencing, VPN setup, behavioral biometrics, AI-based phishing detection, and ongoing education.
Keep in mind that no single technique can provide total safety. However, you may build a strong defense against changing phishing attempts by using a multi-layered strategy to smartphone security. Nowadays, protecting your smartphone is more of a need than a choice. Keep yourself updated, exercise caution to prevent and protect your gadget from possible dangers.
What is smartphone phishing?
Phishing is the term used to describe dishonest attempts to obtain personal information using bogus websites, SMS, or emails on smartphones. Attackers impersonate trustworthy businesses to trick customers into clicking on dangerous links or disclosing personal data like credit card details, passwords, or social security numbers.
How can I tell if my phone is being phished?
Phishing can be identified by unusual app activity, strange pop-ups, or unwanted emails or texts with urgent requests. Phishing websites often differ significantly in appearance or URL, even though they may look similar to legitimate ones.
What are common phishing attacks on smartphones?
Malicious URLs in emails, SMS, social media, and phony apps are examples of common techniques. Fake website pop-ups, AI-generated emails, and QR codes are also being utilized more frequently to trick users into installing malware or disclosing private information.
What should I do if I fall for a phishing attack?
Report the incident to your bank or credit card company, change your passwords immediately, and notify any other services that might be affected. Watch your accounts for any fraudulent activity, and consider running an antivirus scan.
How can I protect my smartphone from phishing attacks?
Update your operating system and programs, avoid unknown URLs and enable two-factor authentication. Behavioral biometrics, DNS filtering, and a VPN all help to increase security.
Can phishing attack happen on Android or iOS phones?
It’s true that phishing attacks can affect both iOS and Android phones. Even though iOS frequently has better protection, both platforms are vulnerable to phishing tactics such malicious URLs, fake apps, and fraudulent conversations.
What is DNS filtering for smartphones?
DNS filtering blocks access to risky websites by intercepting DNS requests. By preventing your device from connecting to malicious or fraudulent websites, it provides an additional layer of protection against online threats.
Is multi-factor authentication enough to prevent phishing attacks?
Multi-factor authentication (MFA) is not perfect, even though it works well. Phishing attempts that trick you into disclosing authentication codes can still get around MFA. MFA should always be used in conjunction with other security measures, like avoiding suspicious links and performing regular upgrades.
What is the role of VPN in protecting against phishing attacks?
A VPN shields your data from attackers eye by encrypting your internet connection and masking your IP address. By providing additional security when browsing or accessing private data over public Wi-Fi, it reduces susceptibility to phishing assaults.
Can artificial intelligence help detect phishing attacks?
Indeed, AI-powered systems that analyze patterns in emails, webpages, and communications can detect phishing attacks in real time. These tools are faster than individuals at spotting fraudulent behavior and help prevent phishing attacks before they succeed.