7 Best Cyber Hygiene practices for Gen Z and how they matter in 2025
You belong to Generation Z because you grew up in a hyperconnected society. Despite your familiarity with digital life, you are nevertheless susceptible to the growing number of cyberthreats. You might think you’ve heard all there is to know about cyber hygiene: avoid questionable connections, make secure passwords, etc. Those basics are still important, but they are not enough to keep you secure in today’s society. Solutions need to evolve in tandem with the increasing intelligence of cybercriminals.

It’s easy to think that common sense will protect you: avoid suspicious emails, use strong passwords, and never click on suspicious links. The issue is that the risks of today go beyond what we usually think of as “basic security.” If you want to ensure that your digital life stays safe and secure, you need to employ innovative, next-level strategies and go beyond general guidance.
In this article, we’re exploring fresh, feasible options for implementing Cyber Hygiene practices for Gen Z immediately. Instead of only focusing on risk avoidance, let’s make sure you have proactive, state-of-the-art cyber hygiene solutions that are easy to incorporate into your daily routine. Get ready to explore the topic of digital safety in greater detail.
Table of Contents
You’re Leaving Open Doors for Cyber Criminals
Despite greater knowledge, Gen Z remains one of the most vulnerable demographics. Why? Because you regularly use a range of online platforms, including gaming apps, Instagram, and TikTok, without taking the necessary safety measures to properly protect those websites.
We recognize that, given your busy schedule, adding an additional security step may seem like a burden. However, the cost of doing nothing is far greater than the inconvenience of taking a few more steps to protect your digital life.
The problem is that most people continue to practice cyber hygiene using outdated, basic techniques that are no longer relevant. Basically, if you use traditional methods like using weak passwords, using the same login credentials on many sites, or not using encryption, you’re giving thieves a free pass. The intricacy of contemporary cyberattacks, such as AI-powered malware and phishing 2.0, requires more advanced solutions.
Why the Same Old Tips Aren’t Enough
It’s easy to overlook the risks and think, “I won’t be affected.” The issue is that you are more exposed than before. According to a 2024 estimate by Cybersecurity Ventures, the global annual cost of cybercrime is expected to reach over $10 trillion by 2025. This isn’t just a statistic; it’s currently affecting people just like you.
Think about it: Have you ever posted something on social media that gave away more than you intended to? Or have you ever used public Wi-Fi to conduct online banking? Cybercriminals can exploit these seemingly harmless actions.
Now consider how you would feel if you saw a friend’s account hijacked or a private piece of information exposed. In addition to the financial loss, there is also invasion of privacy, stress, and constant worry about what might happen next. Gen Z is more vulnerable to this than any other generation because of the intimate relationship between your digital and real-world lives. Every online activity you take increases the likelihood that hackers will be able to get your personal information, and the consequences are becoming more severe.
From TechRadarPro’s recent report on agentic AI threats (July 2025)
“Traditional cybersecurity approaches focused on system protection and one‑off employee training are insufficient.” The article warns that autonomous AI agents can scale phishing, credential stuffing, and reconnaissance—meaning static defenses and reactive posture are increasingly inadequate. link
Advanced Cyber Hygiene practices for Gen Z
Let’s examine some professional-level, achievable, and practical advice on keeping appropriate Cyber Hygiene practices for Gen Z instead of restating the same old advice you’ve heard a thousand times. These strategies are designed to tackle the specific challenges you face as a gen-zier and offer new approaches to protect your online life from both common and sophisticated threats.
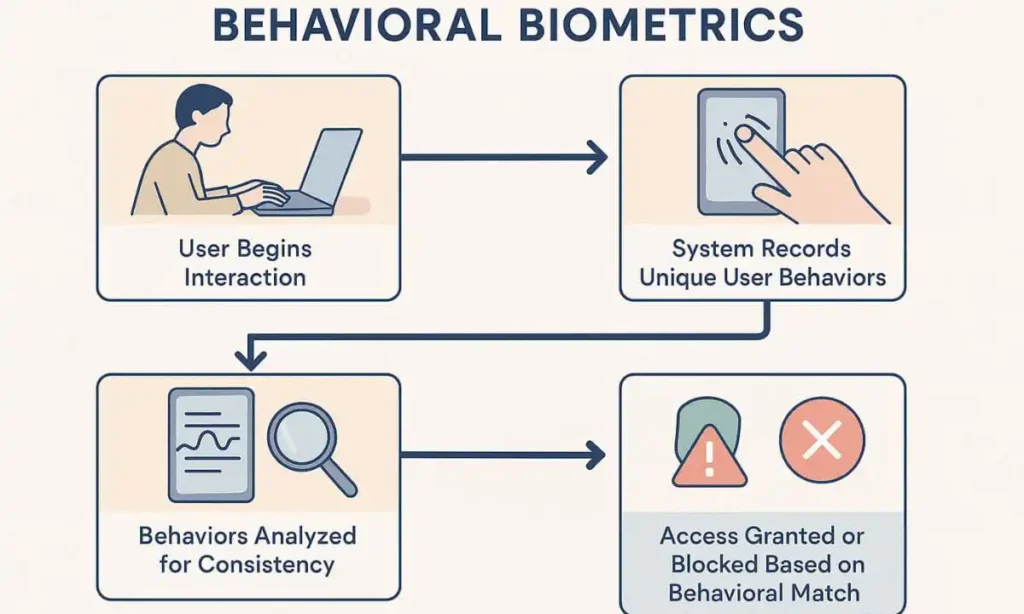
1. Adopt Behavioral Biometrics for Your Online Accounts
Let’s make Cyber Hygiene practices for Gen Z even more robust. Simply using a password is not enough, and advanced phishing or SIM-swapping techniques can even circumvent two-factor authentication (2FA). So what should a Gen Zer do?
A new method called behavioral biometrics looks at how you use your phone, including how you type, swipe, and even hold it. Behavioral Biometrics offer an extra layer of security that is harder for hackers to replicate. This can be included in programs that require a high level of security, such as financial or email services.
How to Implement: Behavioral biometric features are starting to be included in BehavioSec and other advanced password managers and applications. Look for these tools or use this function as often as possible. Even though it isn’t very popular right now, it is the internet security method of the future.
Real-World Example: According to a recent study by Forrester Research, account takeover incidents decreased by 40% in companies that used behavioral biometrics. You may drastically lower the likelihood of illegal access to your accounts by implementing this technique.
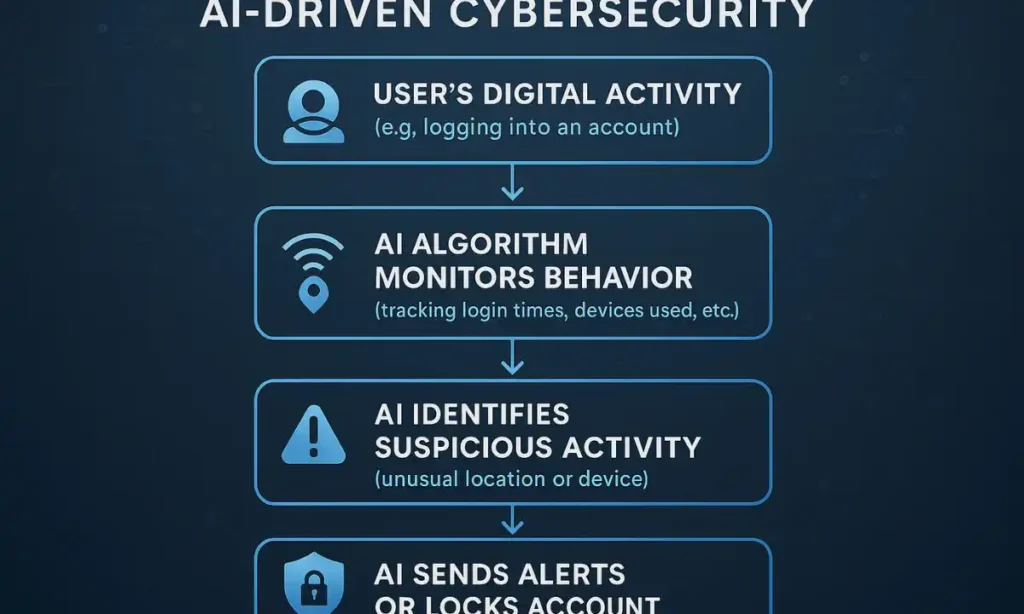
2. Incorporate Artificial Intelligence into Threat Detection
This is a game-changing concept: employ AI to quickly spot suspicious behavior. AI-based personal cybersecurity solutions are now more accessible than ever before, despite the fact that it may appear like a duty best left to companies. These apps can implement Cyber Hygiene practices for Gen Z and keep an eye out for anomalies in your online behavior, such as unwanted device access or logins, and alert you before something goes wrong.
How to Implement: The business could undergo a change thanks to AI-powered apps like Aura that recognize and respond to online threats. Set them up to monitor your accounts, credit cards, and other personal data. By swiftly alerting you to threats like identity theft or fraudulent charges, they will provide you with an additional layer of security
Real-World Example: One Aura user reported that the AI algorithm had identified several unauthorized attempts to access their social media accounts before any damage was done. Because of the early notification, the user was able to change passwords and activate other security measures.
In its July 2025 report, TechRadarPro notes that AI‑based Managed Detection and Response tools can spot subtle anomalies—suspicious logins or lateral movement—and stop threats before they escalate.
3. Use the Power of Virtual Private Networks (VPNs) with Split Tunneling
While VPN services are an excellent initial line of defense when using public Wi-Fi, they are not all created equal. Although “Use a VPN” is the typical advice, there are other options as well. To take things a step further for applying best Cyber Hygiene practices for Gen Z, think about using split tunneling, a feature that allows you to route some of your data through a private VPN while allowing other traffic to bypass it.
Why would you want this? It’s simple: Sometimes using a VPN for all of your traffic will cause your internet speed to drop. Split tunneling allows less risky activities, like surfing, to continue without experiencing further slowdown while preserving control over sensitive ones, including social networking and online banking.
How to implement: Choose a VPN service that offers split tunneling. Providers like NordVPN support this capability. Make sure that only the most critical traffic passes through the VPN tunnel.
Real-World Example: One Reddit user described how split tunneling made it possible for them to stay private while playing games, guaranteeing that their online communications were secure while maintaining their surfing speed.
In its February 2025 analysis, Ascendant USA explains that split tunneling “enhances both security and performance” by sending only crucial data through VPN while bypassing non‑essential traffic.
4. Use Zero-Trust Security Models for Personal Devices
While zero-trust security is often discussed in connection to large enterprises, it is equally important for individual devices as you want to implement advance level Cyber Hygiene practices for Gen Z. A zero-trust approach basically states that you should never assume that a network or device is secure, even if it is located within your home or has previously been trusted.
What do you think about this? A great place to start is by segmenting your devices and networks. For example, don’t utilize the same Wi-Fi network for your business laptops and personal devices. Using a different device for financial tasks, like online banking, from your social networking or gaming accounts improves security and lowers the chance of cross-contamination in the event that one device is compromised.
How to implement: Consider using a home router with built-in network segmentation. Many routers from companies like Netgear and Linksys allow you to create separate “guest” networks for your Internet of Things (IoT) devices, allowing you to keep your laptop, phone, and other personal devices on a more secure network.
Real-World Example: Some IT enthusiasts described how they were able to stop a major malware attack by implementing a zero-trust strategy. They prevented a breach that might have depleted their accounts by keeping their laptop and game console apart from their financial equipment.
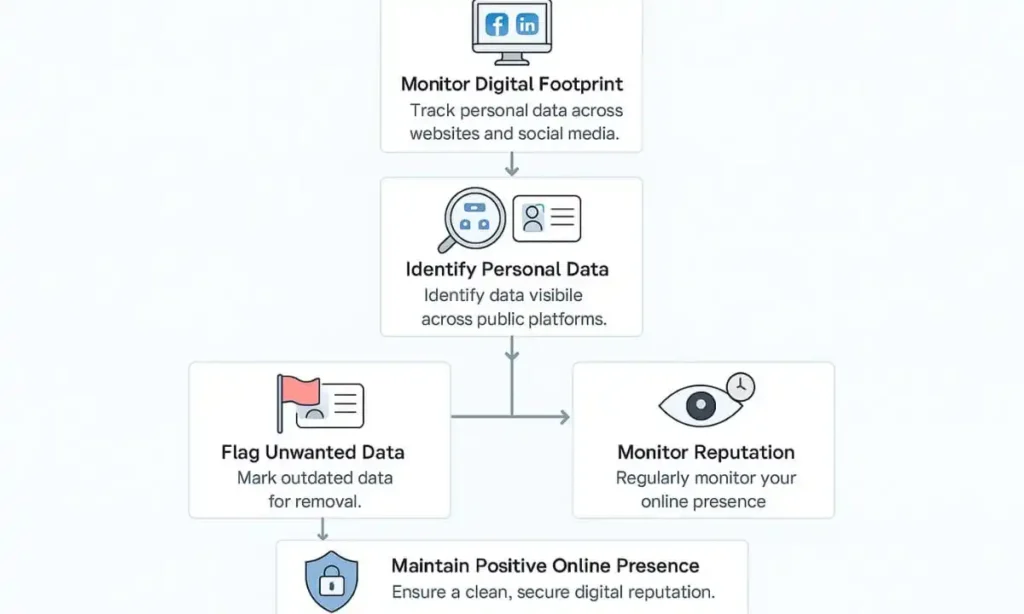
5. Digital Footprint Monitoring and Reputation Management
A lot of us don’t realize how much personal information we provide online. Your digital footprint, or the trace of your personal data across several websites, social media accounts, and other online platforms, might be a gold mine for identity thieves.
Observe your digital footprint carefully if you wish to truly practice good cyber hygiene practices for Gen Z. Services like DeleteMe and BrandYourself can help you find and remove unwanted personal information from search engines, data brokers, and public websites. You lessen the chance that your personal information may be exploited by doing this.
How to implement: Sign up for a service that helps you get rid of your digital footprint. These technologies may ensure that outdated personal data is never left online by automating the data cleanup procedure. Additionally, set up Google Alerts for your name to keep an eye on what people are saying about you online.
Real-World Example: A woman utilized BrandYourself to clear out public directories of old photographs and out-of-date personal data. Her internet privacy was greatly enhanced in a matter of weeks, and she felt more secure knowing that her information wasn’t being stolen.
6. Use Encrypted Messaging Services and Email
Email providers and end-to-end encrypted messaging services are essential in a world where privacy is always being violated. Only you and the designated receiver will be able to read the messages thanks to these services. This degree of security is provided by well-known messaging programs like Signal and WhatsApp, guaranteeing that your communications are kept private, even from the service providers themselves.
For email, think about using ProtonMail, which provides free encrypted email services that guarantee the security of your private correspondence.
How to implement: Always use an encrypted app like Signal when transmitting critical information or having private conversations. Use ProtonMail or Tutanota instead of Gmail for emails since they provide strong encryption. All these apps are really good Cyber Hygiene practices for Gen Z to implement in a world full of threats on daily basis.
Real-World Example: An advocate for digital privacy revealed that they never had another email hack after moving to encrypted services. This small adjustment strengthened defenses against identity theft and phishing scams.
7. Master the Art of Risk-Based Social Media Sharing
Most individuals would suggest that you check off your social network privacy settings. If you decide to go farther, though, use risk-based sharing. The objective is to evaluate the potential risk of sharing a post based on the platform and to implement best Cyber Hygiene practices for Gen Z specially.
It’s OK, for example, to share a vacation photo with a few chosen friends. Posting details about your location or employment to a wider audience, however, could put you in danger. Consider the details, like your location or the agenda for your next vacation, that could expose you to social engineering attacks.
How to implement: Stricter privacy settings on social media should be put in place, but you should also consider the risk of your posts. Check your settings often to ensure they reflect your current sharing in order to follow good Cyber Hygiene practices for Gen Z.
Real-World Example: By using a vacation photo to predict when they will be away from home, an Instagram influencer revealed how hackers gained access to their account. Because they understood the risks of revealing such material in public, they were able to stop similar incidents from happening again.
Conclusion:
Use Advanced level Cyber Hygiene practices for Gen Z to Take Charge of Your Digital Life Making complicated passwords and checking out at the end of each session are just two aspects of Cyber Hygiene practices for Gen Z. It means taking proactive steps to protect your entire online presence. Even though Gen Z is the most connected generation, you are the most at risk. By employing cutting-edge techniques like encryption, AI-driven threat detection, and zero-trust security models, you can lower your risks and safeguard your digital life from complex cyberthreats.
Thus, don’t wait for a breach to happen. Implement these Cyber Hygiene practices for Gen Z immediately. Keep your gadgets safe, minimize your digital footprint, and exercise caution when sharing sensitive information online. The internet may be a really helpful tool if you know how to utilize it properly.
What is behavioral biometrics and why should Gen Z use it for cybersecurity?
One of the most advanced Cyber Hygiene practices for Gen Z is to use behavioral biometrics to measure how you type, swipe, and handle your phone. Unlike passwords or even two-factor authentication, this approach is unique to each user and impossible to copy, reducing the risk of unauthorized access.
How can artificial intelligence improve personal cybersecurity for Gen Z?
AI-based threat identification is an excellent Cyber Hygiene practices for Gen Z. AI tools can detect unusual behavior, such as suspicious login attempts, and warn you right away. This enables Generation Z consumers to act swiftly and prevent identity theft or data breaches before they do significant damage.
Why should Gen Z consider using VPNs with split tunneling instead of regular VPNs?
Split tunneling using a VPN is a significant improvement in Cyber Hygiene practices for Gen Z. It secures sensitive operations like banking, while less risky browsing bypasses the VPN, allowing for faster internet connections while maintaining anonymity. It provides an excellent blend of performance and protection for everyday usage.
How do I protect my personal data from data brokers?
Data brokers collect and sell personal information. To protect your data, use programs like DeleteMe or BrandYourself that remove your information from public databases. Use Google Alerts to track the spread of your data and regularly review your online footprint.
Why should Gen Z use encrypted messaging apps and email services?
Using encrypted apps like Signal and ProtonMail is one of an essential Cyber Hygiene practices for Generation Z. These solutions ensure that only you and the intended recipient can see your messages, keeping your private conversations safe from hackers, data collectors, and even the platforms themselves.
How does a zero-trust security model benefit personal cybersecurity?
A zero-trust approach is one of the proactive Cyber Hygiene practices for Gen Z that ensures no network or device is automatically trusted. Gen Z consumers can prevent malware propagation by segregating their work, gaming, and financial gadgets, lowering the danger of a single hack infecting everything they use.
Why should I use a password manager over storing passwords in my browser?
Password managers protect your credentials from unauthorized access by securely storing and encrypting them. Unlike browser storage, which is vulnerable to viruses, password managers generate strong, unique passwords and protect them using state-of-the-art encryption. This significantly reduces the likelihood of account takeovers.
What are the most common cyber threats?
Common cyberthreats include ransomware, malware, phishing attacks, data breaches, and identity theft. Because these threats often exploit human error, outdated software, and inadequate security protocols, it is imperative to stay vigilant and up to speed on security measures.
How can I protect my social media accounts?
To keep your social media accounts safe, limit the amount of personal information you provide, use two-factor authentication, make sure each account has a strong, unique password, and frequently check the privacy settings. Avoid clicking on links and accepting requests from people you don’t know.
What is digital footprint monitoring, and how does it help protect Gen Z?
Monitoring your digital footprint is one of an important Cyber Hygiene practises for Gen Z. It comprises locating and removing personal information from public directories and search engines in order to prevent identity theft. Tools like DeleteMe automate this process, allowing Generation Z to maintain their privacy in an increasingly exposed digital environment.